WizardOfBoz
Diamond
- Joined
- Sep 30, 2006
- Location
- SE PA, Philly
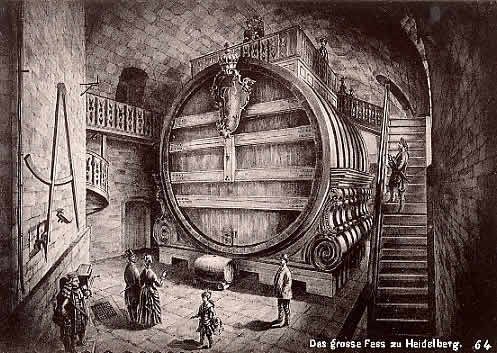
Ok, I was in Germany last summer (Heidelberg is awesome, and I got to eat dinner in the castle and saw the "Heidelberg tun*). Bought a Vodafone and a German SIM card. I will be in Italy in a couple weeks (Venice, I know, my life sucks) and want to know if I can use the locked German Vodafone in Italy. In other words, will a German locked vodaphone accept an Italian SIM card, or do I need to use another phone?
A separate question is about Verizon (my carrier). I have a GSM phone (Droid RAZR) with a US SIM. I know I can buy European service from Verizon, but it's insanely expensive, like a Euro a minute. Has anyone figured out a cheaper way to use Verizon in Europe? I have no problem paying for service, but it seems that the mobile companies realize that I can use Skype for most calls and they are going to ream me for using my handset. The other business model would be to price minutes low enough so that I used the thing a lot and didn't hate Verizon, but I guess that's a decision better made by some flippin' 27 year old MBA at Verizon than me, a mere customer.
Last, can I set up a local Italian number via Skype so that I can use the mobile to call a local Italian number and have that relay home to the states, without the international charges?
Any and all advice appreciated.
Jim
*A big carved oak wine cask. Actually, the worlds largest. It built in 1751 from the trunks of 130 oak trees and has a capacity of 58,124 gallons. It is 28 feet deep by 23 feet high. The balustraded platform on top was built as a dance floor.
A separate question is about Verizon (my carrier). I have a GSM phone (Droid RAZR) with a US SIM. I know I can buy European service from Verizon, but it's insanely expensive, like a Euro a minute. Has anyone figured out a cheaper way to use Verizon in Europe? I have no problem paying for service, but it seems that the mobile companies realize that I can use Skype for most calls and they are going to ream me for using my handset. The other business model would be to price minutes low enough so that I used the thing a lot and didn't hate Verizon, but I guess that's a decision better made by some flippin' 27 year old MBA at Verizon than me, a mere customer.
Last, can I set up a local Italian number via Skype so that I can use the mobile to call a local Italian number and have that relay home to the states, without the international charges?
Any and all advice appreciated.
Jim
*A big carved oak wine cask. Actually, the worlds largest. It built in 1751 from the trunks of 130 oak trees and has a capacity of 58,124 gallons. It is 28 feet deep by 23 feet high. The balustraded platform on top was built as a dance floor.






 My wife and her sister are planning on going back for the month of October.
My wife and her sister are planning on going back for the month of October.